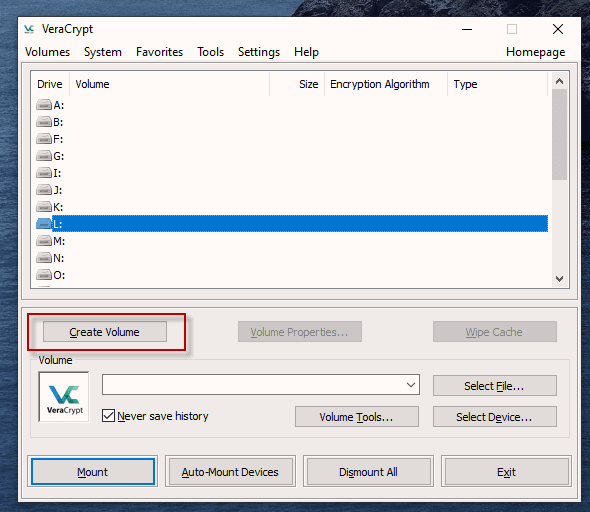
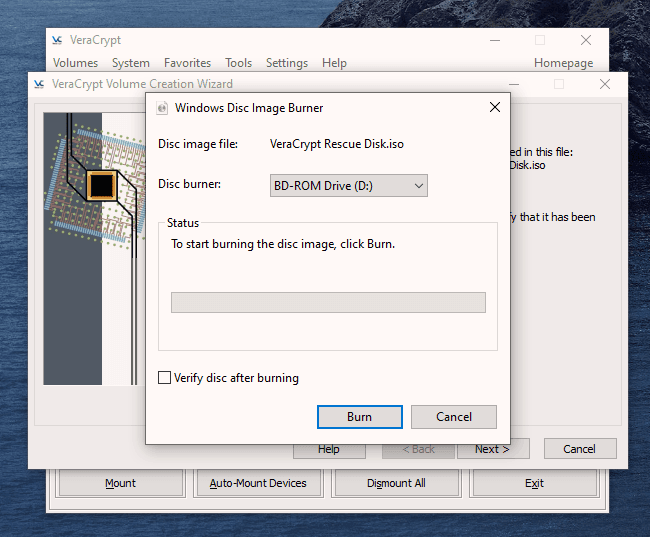
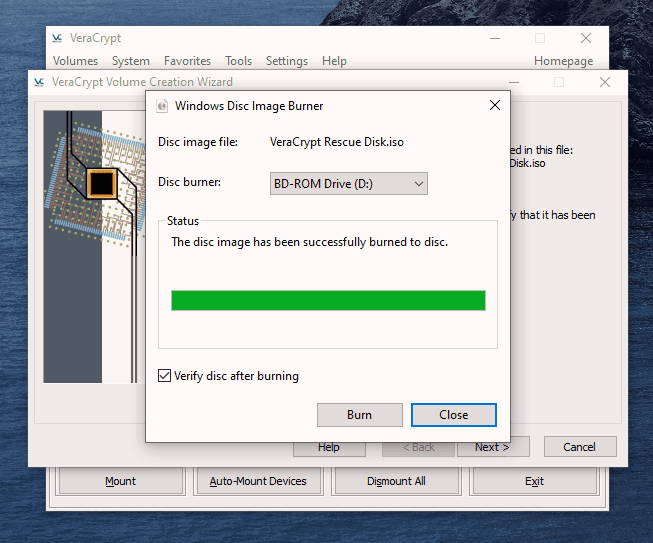
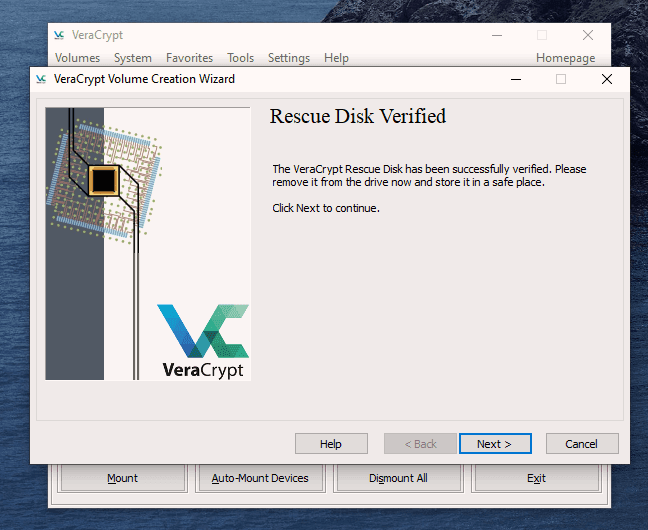
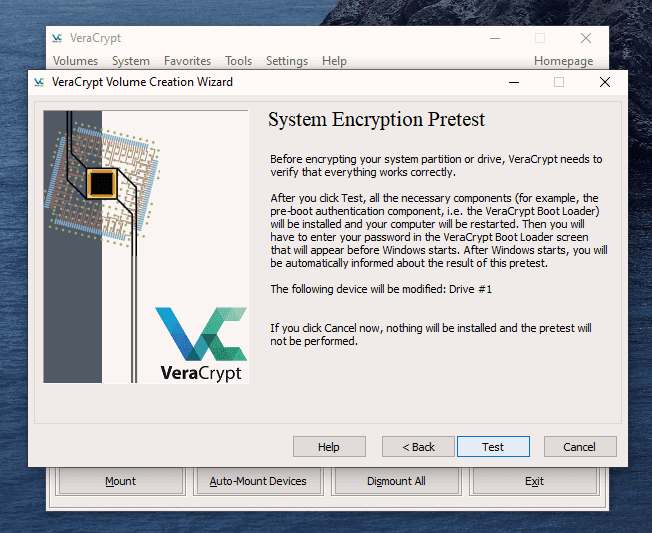
But now we’re going to up the ante and encrypt the hard-drive. After a few stiff drinks to build up the courage, it’s time to get this show on the road.
How To Encrypt Your Windows Hard-Drive To Keep Out Snoopers
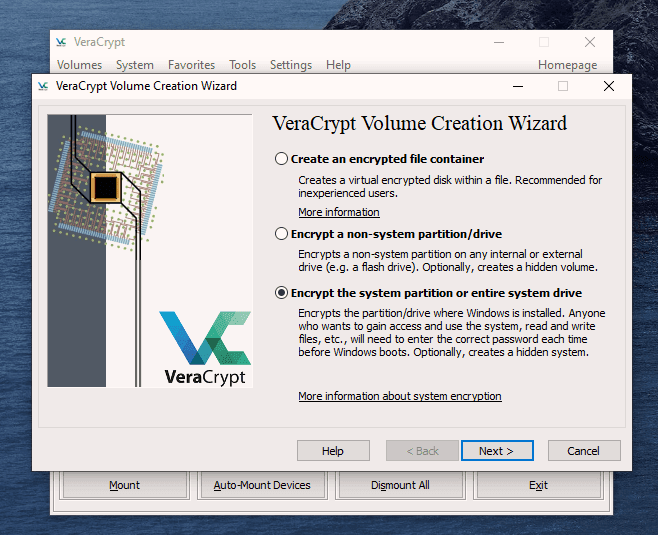
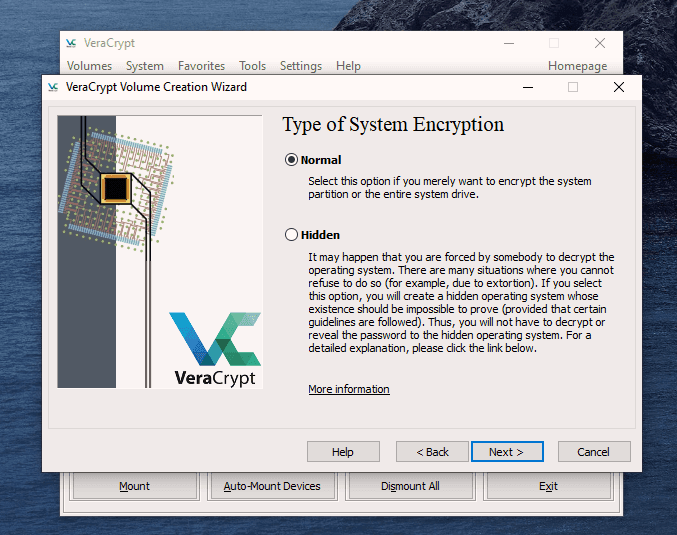
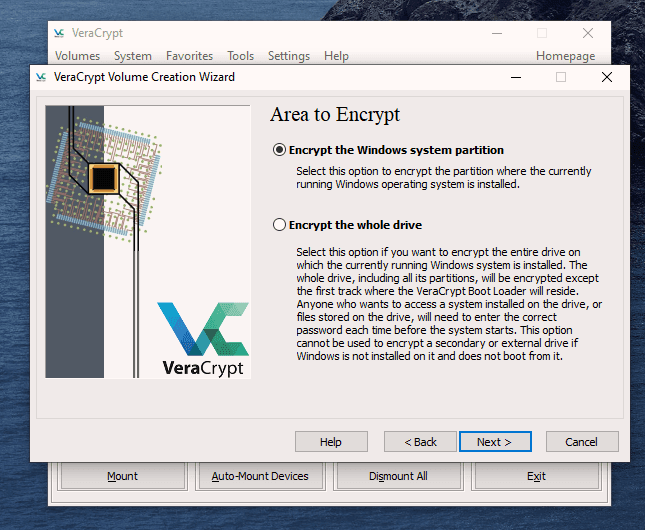
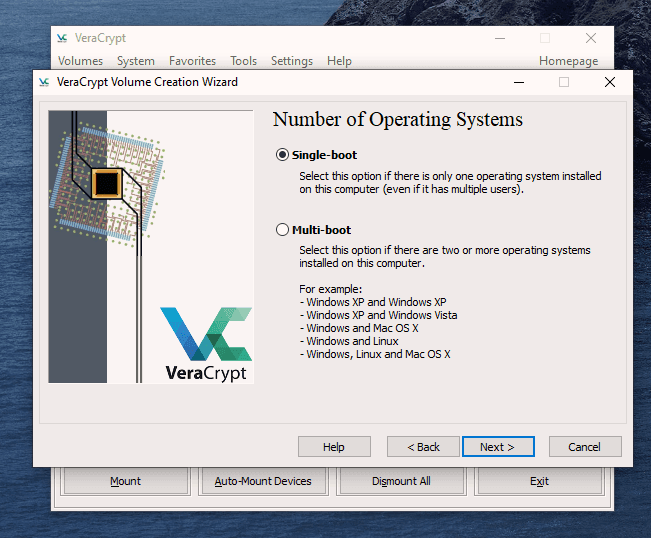
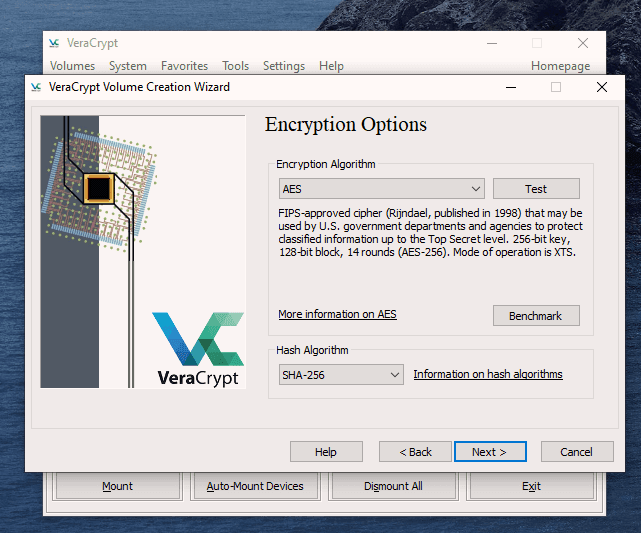
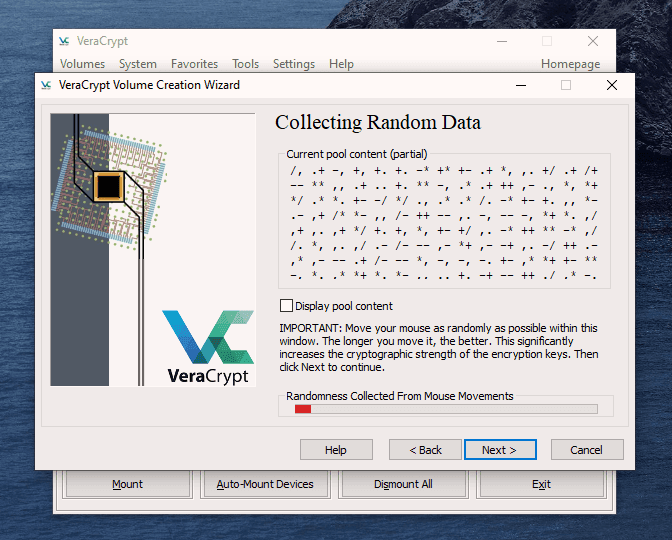
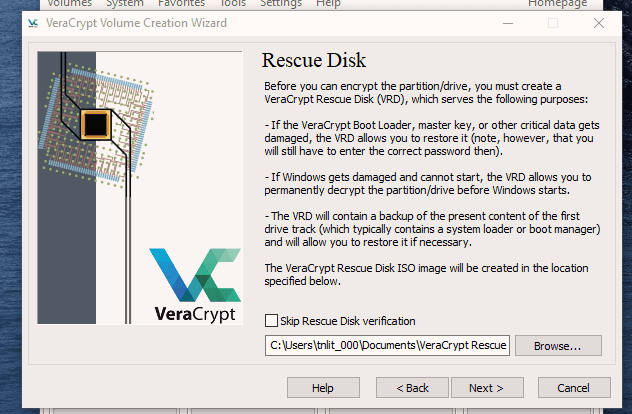
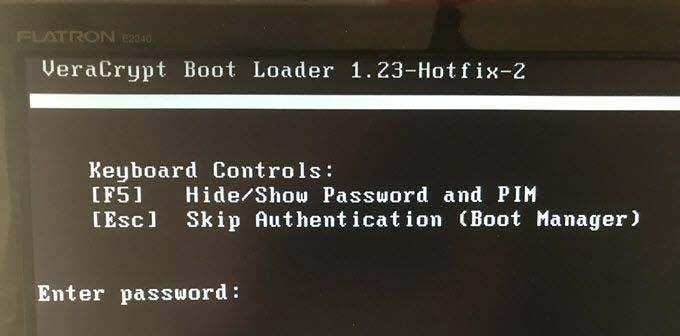
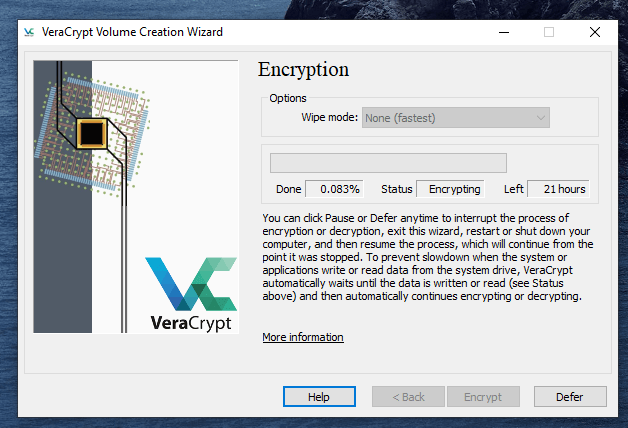
This is actually not too difficult to do. Just follow these steps in order and hopefully your computer won’t explode in your face. I’m assuming you already have VeraCrypt installed but if not, you can get it here. First, open up VeraCrypt and click on “Create Volume”. You will then see three options. We have already done the first two in previous articles. Today we are going for option number three – “Encrypt the system partition or entire system drive.” Click “Next” to proceed. In this case, we are going for a normal encryption, not a “hidden operating system”. So choose the first option and click “Next” to move on. I personally feel (although you may disagree) that you only need to encrypt the part of the hard drive with the Windows operating system on it. Keeping it simple (which is always a mantra of mine), I went for option one – “Encrypt the Windows system partition.” You may decide to choose the second option but if you do, you will get lots of warnings about the consequences if it all goes wrong. If you only have Windows on your computer then you have a single-boot system. If you have multiple operating systems (say Windows and Linux for example) on your computer, then it’s a multi-boot system. So choose which one you have. It will now ask you which encryption option you want. But as I have indicated in the previous articles, unless you have a particular reason why, you should leave the encryption protocols on the defaults. This is the AES standard used by governments to encrypt secret documents. Also leave the hash-algorithm as it is. Click “Next”. After specifying your desired password, it is time to generate your encryption keys. To make them as strong as possible, you need to move your mouse or trackpad around the VeraCrypt window in a “random order”. As you do so, the bar at the bottom will go from red to yellow to finally green. When the green bar is fully at the far right-hand end of the screen, click “Next”. Since you are now encrypting a hard-drive (or part of one), you need to take an extra cautionary step in case you lock yourself out of your hard-drive. This is called the VeraCrypt Rescue Disk (VRD) which will repair any damage to the VeraCrypt boot loader or to Windows, allowing you to (hopefully) log in. However, it is not a security risk having this rescue disk as you will still need the encryption password for it to work. VeraCrypt will select an area for your rescue disk to be placed once it is created. But you can easily move it to another location if you want, by clicking the “Browse” button. Do NOT deselect “Skip Rescue Disk verification” – that is essential. Click “Next”. This next step opens up the Windows Disc Image Burner. You will see that the rescue disk is an ISO file and you need to choose the disc burner on your hard-drive. A normal 700MB CD disc is sufficient. Select “Verify disc after burning.” Once the disc is in your burner drive, click “Burn” to start the process. When the process has been finished, the disc burner will open its tray in the hard-drive. Close the tray again, let the disc run, so Disc Image Burner can verify the disc to make sure everything worked OK. Hopefully, you will eventually see this. It’s now time for VeraCrypt to do some pre-testing before it starts encrypting your hard-drive or partition (depending on what you chose). As the next screenshot says, your Windows system will restart, the boot loader will be installed and assuming all went well, the system will begin encrypting. Click “Test” to begin that process. When the computer restarts – before Windows loads – you will now see the following screen. Enter your password in the space provided. You probably didn’t specify a PIM in the password settings (I didn’t) so in that case, leave it blank when it asks you for a PIM and hit enter. Now wait for your system to log in. If it’s the first time you’re doing this, the log in process might be slightly delayed. Once your password has been successfully verified, your system will begin encrypting. As you can see it takes a long time to encrypt the system, depending on how big it is, so this might be one of those times when you need to leave the computer on overnight in order for it to do its thing. Once it’s done, your computer is a lot more secure. Now cackle with satisfaction when your nosy roommates futilely try to break into your computer to read your love letters to your unrequited love.